Unbreakable Database Security at Your Disposal
Your Database is Only as Secure as Your Method of Storage.
The weakest link in security is centralized architecture. Data breaches and hacks are a recurring theme due to conventional database storage. ZK Face Proof, the world’s first zk-proof with facial authentication ensures only verified, live users— encrypt and decrypt their own data in a distributed manner.
INTRO
Why Databases Get Hacked
Stop Storing Sensitive Data. Start Securing Trust.
Cybercriminals don’t look just for data, but for sensitive and private data. Current databases often store public, sensitive, private, and confidential data using uniform methodologies, which can contribute to data breaches in industries such as telecommunications, banking, and e-commerce.
Centralized Databases Are Vulnerable – A single break in can expose millions of records.
Software Patches Signals Architectural Flaws – Cybersecurity budgets keep increasing, but so do data breaches.
Passwords Are Easy to Hack – Phishing, brute-force attacks, and social engineering are effective methods to hack user’s data.
ZK FACE PROOFS
ZK Face Proof: The End of Data Breaches
Distributed Storage. Local Encryption. Self-custody Data.
Users’ data should belong to users—Not hackers. Traditional databases rely on securing user data in a centralized manner, making them lucrative targets for cybercriminals. ZK Face Proof eliminates the centralization of sensitive data and by migrating it to the blockchain, it ensures no single point of failure is left for attackers to exploit.
Why Choose ZK
Face Proof?
Self-Custody Data
With traditional security systems, companies take custody of data-subjects information. With ZK Face Proof, users own and control their data and credentials, which ensures their personal information stays secure and private.
Self-Custody Data
With traditional security systems, companies take custody of data-subjects information. With ZK Face Proof, users own and control their data and credentials, which ensures their personal information stays secure and private.
Self-Custody Data
With traditional security systems, companies take custody of data-subjects information. With ZK Face Proof, users own and control their data and credentials, which ensures their personal information stays secure and private.
Zero-Knowledge Face Proofs (ZKFPs)
Unlike traditional facial recognition, ZKFPs don't store or share user biometrics. Instead, it uses cryptographic proofs to verify a user’s identity without revealing or retaining any sensitive facial data.
Enterprise-Grade Liveness Detection
Cybercriminals use deepfake videos, 3D masks, and static photos to bypass facial verification. ZK Face Proof integrates advanced liveness detection to prevent all forms of biometric spoofing to ensure only real users gain access.
Seamless Global Compliance
Regulatory compliance is no longer a headache. ZKFP meets GDPR, PCI-DSS, PSD2, and other major data security standards, making it easier for enterprises to operate in regulated industries without compliance risks.
Why Databases Get Hacked
Stop Storing Sensitive Data. Start Securing Trust.
Cybercriminals don’t look just for data, but for sensitive and private data. Current databases often store public, sensitive, private, and confidential data using uniform methodologies, which can contribute to data breaches in industries such as telecommunications, banking, and e-commerce.

HOW IT WORKS
How ZK Face Proof Works
Security-First Data Custody

User Initiates Onboarding

A user accesses a platform, chooses a username and proceeds to register their personal information.
Live Face Scan & Anti-Fraud Checks

The system captures a real-time facial scan while detecting deepfake and spoofing attempts.
Zero-Knowledge Proof Generation

Without sharing raw biometric data, an encrypted cryptographic proof of the registration is created in the form of a QR code.
Instant Verification & Ongoing Access

The proof is matched against encrypted records to grant access in seconds—without ever exposing sensitive data.
The Data is Safely Stored

Every user gets a ZK Face Proof, represented in a QR code. This code can be safely stored in any database architecture, but it can only be decrypted by the data subject —enabling GDPR compliance.
ZK Face Proof delivers seamless, unbreakable data management—without the risks of traditional data storage.
INDUSTRIES
Seamless Cybersecurity for High-Risk Industries
Frictionless User Verification with Privacy-First Authentication
ZK Face Proof brings the highest level of security to industries where identity fraud and data breaches are common. By eliminating biometric storage and using zero-knowledge cryptography, it ensures secure authentication with just a password and simple facial scan—no data risks.
Telecom – Stop SIM Swap Fraud & Fake Activations
Weak identity checks lead to SIM swap fraud and unauthorized activations. ZK Face Proof stops fraud before it happens.
- Secure SIM Registrations – Verify users with real-time facial authentication.
- Prevent SIM Swap Attacks – No more hijacked numbers or unauthorized transfers.
- Reduce Fraud Costs – Minimize identity-related customer disputes.
Banking & Fintech – Fraud-Proof KYC & Transactions
Financial institutions face increasing risks from identity theft and compliance failures. ZK Face Proof ensures secure, seamless KYC and transactions.
- Instant KYC Without Risk – Verify users without storing biometric data.
- Secure Payments & Logins – Authenticate transactions with a quick facial scan.
- Regulatory Compliance – Meets GDPR, PSD2, and financial security standards.
E-Commerce – Secure Logins & Frictionless Checkouts
Account takeovers and payment fraud can devastate online businesses. ZK Face Proof protects e-commerce platforms with real-time user verification.
- Robust Logins – Eliminate weak passwords break in with secure facial authentication.
- Stop Payment Fraud – Approve transactions only for real, verified users.
- Enhance Customer Trust – Reassure buyers their biometric data is never stored.
INTEGRATION
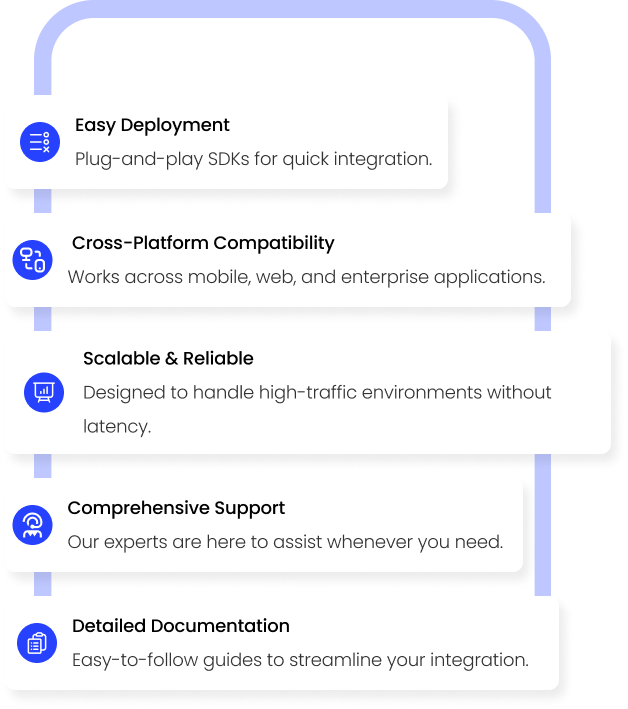
Effortless Integration, Maximum Security
Plug, Authenticate, Secure
ZK Face Proof fits right into your existing systems with our developer-friendly API. Whether you’re running a banking app, an e-commerce platform, or a telecom authentication portal, integration is fast, flexible, and hassle-free.
Your Database. Your Rules. No Unauthorized Entry
Don’t let hackers exploit weak authentication. With ZK Face Proof, access is granted only to those who truly belong.