Revolutionizing Cybersecurity for Digital Businesses
Protect your user's data like never before with ZK Face Proof’s innovative, privacy-first technology.
INTRO
The Future of Data Security is Here - ZK Face Proofs
Stop Storing Sensitive Data. Start Securing Trust.
Every day, hackers sharpen their tools to exploit sensitive and private data of end users. For banks, e-commerce giants, fintech innovators, and digital enterprises, a single breach can mean catastrophic financial loss, legal penalties, and eroded trust.
Secure your sensitive data with ZK Face Proof – the world’s first cybersecurity solution that combines zero-knowledge cryptography with facial recognition to ensure both privacy and protection.
Advanced Technology for Superior Security
Verify identities without storing facial data using the world’s first, user-friendly ZK Face Proof technology.
Enterprise-Grade Liveness Detection
Defeat deepfakes, 3D masks, and photo spoofs.
Blockchain Storage
Move sensitive user data to the blockchain and never worry about data breaches again.
Data Ownership
Give Users full control and custody of their data.
Effortless Global Compliance
Meets GDPR, PCI-DSS, PSD2, and other key regulations.
The Future of Security
Security will come not from a patchwork but an architecture.
George Gilder. Life after Capitalism
FEATURES
History's Worst Hacks, Today's Best Defense: ZK Face Proof
Users’ data should belong to users—Not hackers. Traditional databases rely on securing user data in a centralized manner, making them lucrative targets for cybercriminals. ZK Face Proof eliminates the centralization of sensitive data and by migrating it to the blockchain, it ensures no single point of failure is left for attackers to exploit.
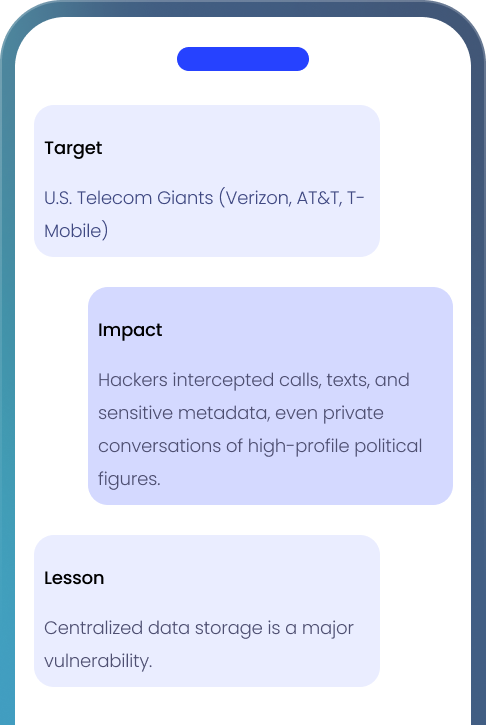
How ZK Face Proof Protects You:
Eliminates centralized storage of sensitive data.
Zero-Knowledge authentication eliminates single point of failure
Even if hackers infiltrate, they find nothing to steal.
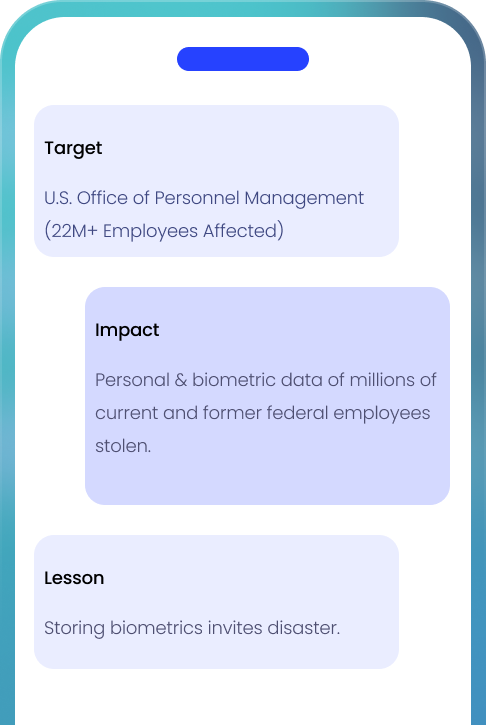
How ZK Face Proof Protects You:
No biometric data storage = no risk of reverse engineering.
Elliptic Curve Cryptography (ECC) ensures total user control.
Prevents breaches that could expose personal identities.
Why wait for the next major breach to take action?
Switch to a security model that eliminates risk from the source!
INTRO
A New Cybersecurity Architecture is Needed
User’s data are all in a relatively few target-rich sites, the potential hackers number in the billions, anonymous and ethereal.
New users bring new vectors of possible attack. Every new user is a possible hacker or hack victim. Software patchwork—grows only additively. It stops one attack vector at a time. Meanwhile attack vectors expand exponentially.
This is not a problem that can be solved with one more privacy patch or even by doubling the money spent on cybersecurity.
The more we spend on internet security, and the more we expand the network, the more vulnerable it grows.
Gilder, George. Life after Capitalism

INDUSTRIES
Uncompromising Security for the World’s Most Targeted Industries
ZK Face Proofs API uses state-of-the-art facial recognition technology combined with zero-knowledge proofs for enhanced privacy. It securely verifies user identities without compromising personal data. By adopting this solution, your business gains an additional layer of cybersecurity that’s impossible to crack, even for the most advanced hackers.
For Banks & Fintechs
Users will have full ownership & custody of their banking data
Secure KYC/AML onboarding with encrypted facial authentication
Complete protection against large-scale breaches like Salt Typhoon

For E-commerce & Digital Platforms
Protect customer profiles & payment data with no storage authentication
One-click, zero-risk checkouts with facial authentication
Say goodbye to hacks like the OPM breach, where massive PII was stolen
For Healthcare & SaaS
GDPR-compliant user verification without storing medical records
Ensure full patient data privacy with zero-knowledge security
Future-proof your system against healthcare cyber attacks

SOLUTION
Integrate
Developer-friendly API with pre-built SDKs for seamless adoption.
Scale
From 100 to 10M+ verifications/month with zero downtime.
No Overhead Costs
Eliminate the use of databases and servers
Act Now—Before the Next Breach Headline
Tomorrow’s Breach is Planned Today. Are You Ready?
Frequently Asked Questions (FAQs)
Unlike traditional systems that store biometric data, ZK Face Proof transforms users’ sensitive information into an encrypted QR code, which can only be accessed through their facial recognition. This means we don’t store any biometric data to protect your customers’ privacy and give them full control over their personal information.
By using zero-knowledge proofs, it verifies identities without storing sensitive user data, making breaches nearly impossible. Even if attackers access your system, they won’t find usable personal information.
Absolutely! ZK Face Proof offers a developer-friendly API designed for seamless integration into your existing authentication and security frameworks. This means you can enhance your data protection measures without the need for a complete system overhaul.
Definitely! Our QR code-based encryption system is lightweight and scalable. Whether you’re protecting data for 100 or 1 million users, our system maintains the same quick response times and 99.99% uptime.
Our no-storage approach to biometric data naturally complies with GDPR, CCPA, PSD2, and HIPAA requirements. Since we don’t store facial data and encrypt all sensitive information, we exceed standard security regulations.

Most clients go live within 2-3 weeks. We provide comprehensive documentation, SDKs for all major programming languages, and dedicated integration support to ensure a smooth setup process.