Imagine losing a customer because your verification process was too slow or confusing. Or worse, letting a fraudster slip through because your system wasn’t strong enough.
Identity verification plays a huge role in both user satisfaction and security. It’s no longer just a formality; it’s part of the experience that defines your brand’s reputation. A well-designed verification process keeps bad actors out while welcoming genuine users without frustration. But how do you create a system that does both?
This blog breaks down practical tips and industry best practices to help you design a reliable identity verification process that keeps fraudsters out and genuine uses in.
What Is Identity Verification, and Why Does It Matter?
Identity verification is the process of confirming the authenticity of a person’s identity to ensure they are who they say they are. This is done by cross-checking government-issued documents, biometric data like facial recognition, and trusted databases to detect any inconsistencies or fraud attempts. It’s a key step in preventing criminal activities such as money laundering, fraud, and identity theft.
For businesses, identity verification isn’t just about security, it’s how you earn your customers’ trust. When customers know their personal information is safe and that the business takes fraud seriously, they are more likely to engage and complete transactions.
Moreover, with increasing regulatory demands worldwide, such as KYC (Know Your Customer) and AML (Anti-Money Laundering) rules, identity verification has become legally mandatory in many sectors. Implementing the right identity verification platform ensures compliance and shields your business from penalties and reputational damage.
Tips for Flawless Identity Verification
To make identity verification truly work for your business, it needs to be fast, secure, and user-friendly. These tips will help you fine-tune your approach and avoid the common pitfalls that cost time, trust, and conversions:
1. Choose the Right Identity Verification Tools for Your Business Needs
Selecting the appropriate tools tailored to your business requirements is crucial for effective identity verification. Each industry and business model comes with different risk profiles and regulatory obligations. For example, a banking platform requires rigorous multi-factor verification, while a social media app might adopt lighter checks balanced with usability. Start by assessing your business’s risk levels and compliance needs.
Look for verification solutions that combine document authentication, biometric verification, and database cross-checking to provide layered security. Also, consider scalability and choose an identity verification platform that can grow alongside your customer base without compromising performance or security.
2. Layer Your Security with Multi-Factor Identity Verification
Relying on a single verification method can leave gaps for fraudsters to exploit. Multi-factor verification strengthens security by combining several checks to confirm user identity. For instance, a user might first submit a government-issued ID for document verification, then complete a biometric check such as facial recognition with liveness detection to ensure a live person is present.
Adding knowledge-based authentication or one-time passwords (OTPs) further verifies that the user controls the claimed identity. This layered approach not only improves accuracy but also deters sophisticated fraud attempts, making it significantly harder for impostors to pass undetected.
3. Use Biometrics for Accurate and Convenient Verification
Biometric verification has revolutionized identity checks by merging high accuracy with user convenience. Technologies like facial recognition compare a selfie or live video against the photo on the user’s ID, while liveness detection prevents spoofing through photos or masks by detecting subtle facial movements and 3D cues.
Biometrics allow users to verify their identity swiftly using their smartphones, thereby removing the need for cumbersome paperwork or in-person visits. This enhances user experience, reducing friction and drop-off rates, while providing businesses with a secure, fraud-resistant verification method that adapts well to mobile-first environments.
4. Cross-Check Against Trusted Data Sources
Beyond verifying documents and biometrics, cross-referencing user information against reliable external databases adds a critical layer of security. Trusted sources such as credit bureaus, government watchlists, and sanctions lists can help identify discrepancies, flag high-risk individuals, or detect synthetic identities.
By integrating these checks into your identity verification workflow, you improve the accuracy of your system and catch fraudulent applications early. This step is especially important in industries with strict compliance requirements or high fraud exposure, ensuring that only legitimate users are onboarded.
5. Optimize User Experience to Reduce Drop-Offs
For businesses, adopting an identity verification solution isn’t just about stopping fraud; it’s about keeping genuine users engaged. A complicated or lengthy process often leads to drop-offs and costs you potential customers. That’s why the user journey should be as seamless as the security is strong.
Look for a solution that’s mobile-friendly, offers clear instructions, and provides real-time feedback to prevent user frustration. Fewer steps, visual cues, and instant error detection can make all the difference. A smoother verification flow doesn’t just improve completion rates, it also reduces support requests and builds trust from the very first interaction.

Best Practices for Smooth and Secure Identity Verification
Following best practices ensures your identity verification process is both secure and easy for customers to complete:
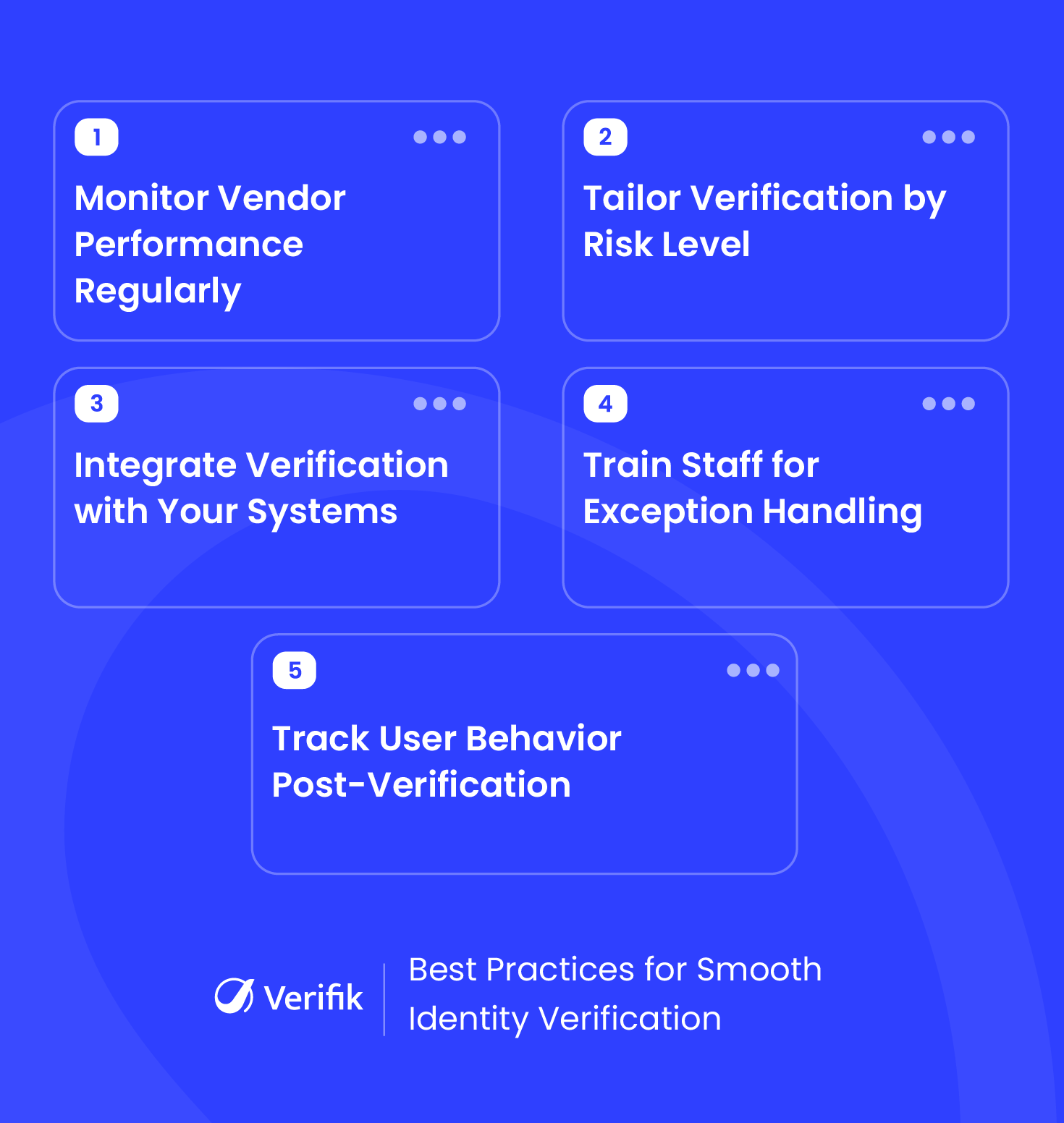
1. Regularly Review Vendor Performance
Choosing an identity verification provider is just the first step. It’s important to keep an eye on how well they’re performing over time. Are they accurate? Fast? Reliable? Regular check-ins and reviews help you catch any issues early and make sure the service keeps up with your business needs and any new regulations. Don’t be shy about giving feedback or asking for tweaks because a credible vendor will always listen to you to solve any issues you might be experiencing. Staying proactive here can save you from surprises that might impact your customers or compliance.
2. Customize Verification Levels by Risk
Not every transaction or customer requires the same level of scrutiny. Collaborate with your provider to set risk-based verification thresholds tailored to your business model. For instance, high-value transactions or new customers from certain regions might trigger more in-depth checks, while returning customers with a clean record can benefit from faster verification. This approach balances security with convenience and improves customer satisfaction without compromising protection.
3. Integrate Verification Data with Your Systems
To maximize the value of your identity verification solution, integrate its data directly with your existing business tools like CRM, fraud management, and customer support platforms. This integration enables real-time insights and automated workflows, helping your teams respond swiftly to potential risks. For example, fraud alerts can automatically trigger account holds or additional verification steps to streamline operations and reduce manual effort.
4. Train Staff to Handle Verification Exceptions
Even the best automated systems encounter cases where verification results are unclear or require further review. Equip your customer service and compliance teams with clear procedures and training to handle these exceptions efficiently. Well-prepared staff can resolve issues faster, guide customers through additional verification steps, and maintain trust, preventing potential revenue loss caused by delays or confusion.
5. Monitor Post-Verification User Behavior
Identity verification is not a one-time event. Use ongoing monitoring tools provided by your verification partner to track user behavior after onboarding. Watch for red flags like unusual login locations, multiple failed access attempts, or sudden changes in transaction patterns. Setting up automated alerts for suspicious activity allows your team to act quickly, prevent fraud, and protect your business reputation without inconveniencing legitimate users.
Wrapping Up
Getting identity verification right builds trust and protects your business without frustrating customers. By applying these tips and best practices, you can maximize the effectiveness of your verification system. Stay proactive, keep the process simple, and monitor continuously to ensure security and a smooth user experience. A well-run verification process benefits both your business and your customers.
Partner with the Leader in Identity Verification
Verifik works hand-in-hand with businesses around the world to provide identity verification that respects privacy and keeps security front and center. Our platform combines advanced facial recognition to securely verify users, real-time ID document validation to detect fakes, passwordless login options to keep accounts safe, and effortless document scanning from any device to speed onboarding; all designed to protect both your business and your customers’ data.
If you want to stop fraud without compromising privacy or user experience, Verifik has the tools to help you get it right. Contact us today to see how our solutions can work for your business!